TeamFence Product
Secure your business with an integrated approach.
BrowserFence

CTEM

TeamFence Product









Protect your employees from browser-based threats without changing their workflow. Minimize human error, eliminate unnecessary IT workload, and ensure regulatory compliance to safeguard costs, data, and systems.






Fency
Find some text to insert here, we want to keep some data (real or fake) to reach truthworty
Most tools protect the device. We protect the person using it. When users face a real threat, we guide them in real time, directly in the browser. No confusion. No waiting. Just clear help, right when it’s needed. A faster, easier way to stay safe.
Forget generic training. Our solution delivers short, targeted education based on the real phishing and web threats your organisation is facing. Users learn from what actually happens, not from abstract scenarios. Relevant. Timely. Actionable.
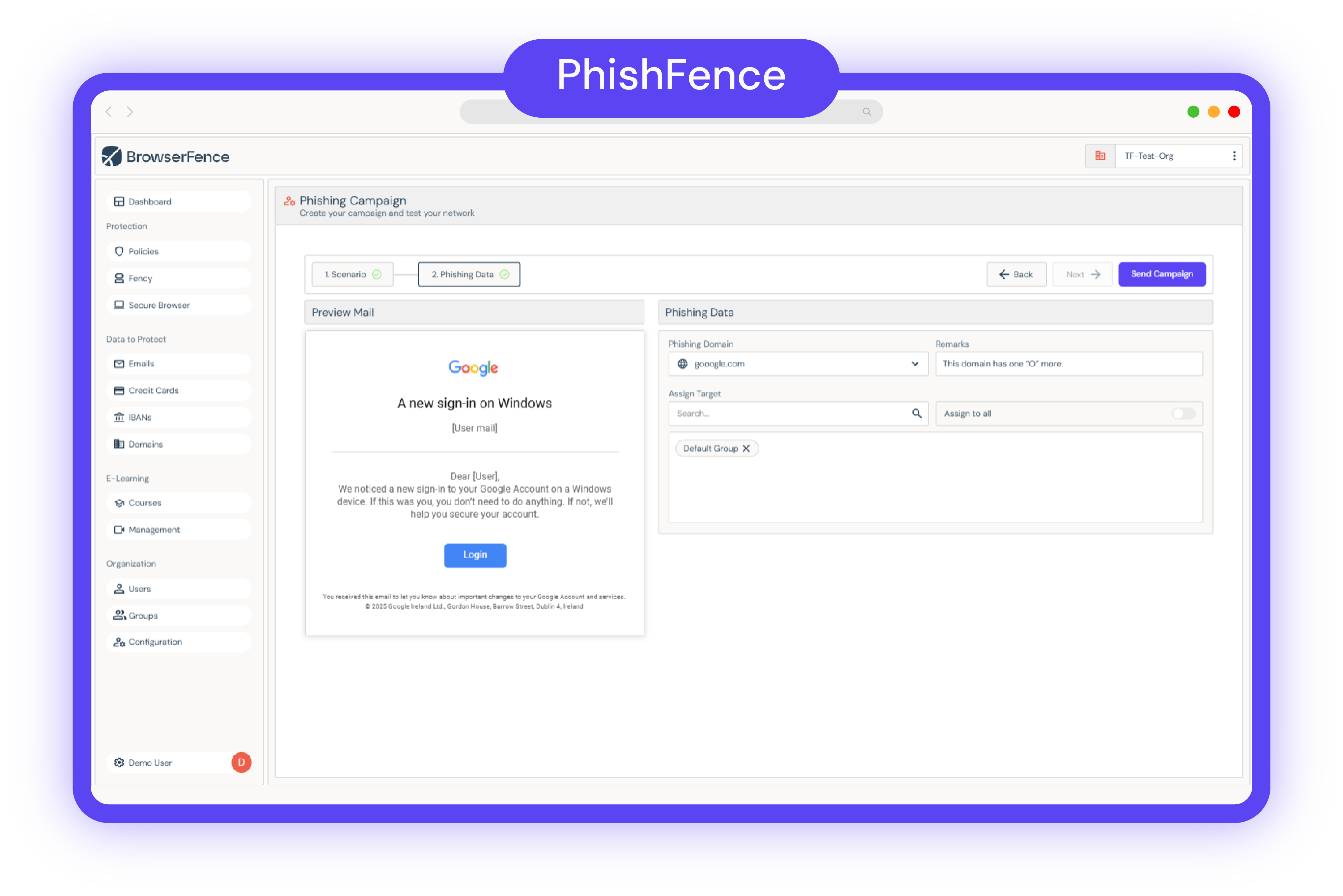
We don’t use random templates. Our phishing simulations are based on the real tools and platforms your users interact with every day, like email, cloud apps, and internal systems. This makes training more effective and behaviour change more natural.
Service Area

How we do it
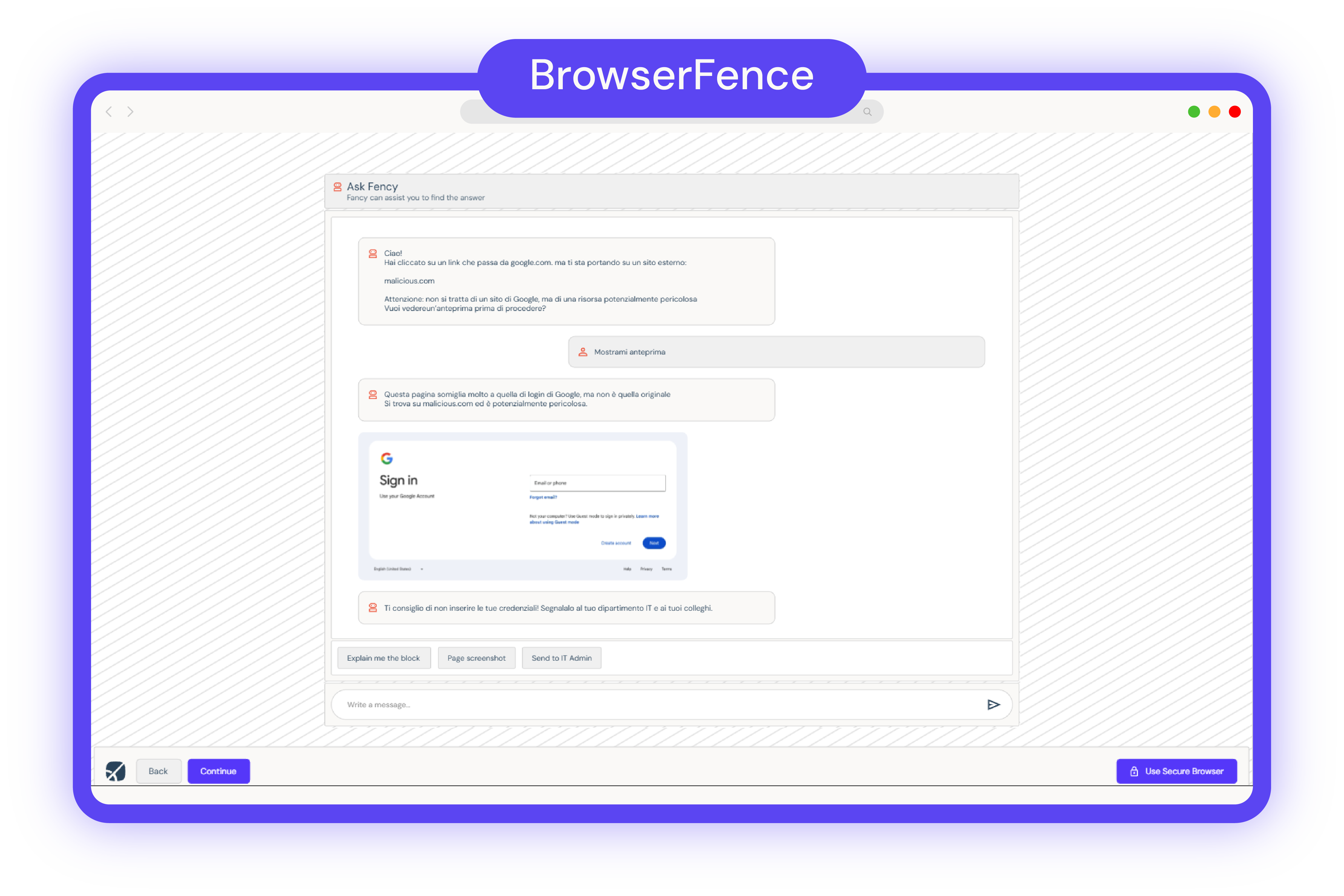
Provides real-time, 24/7 assistance based on user behavior during browsing. It enables users to protect themselves against attacks through various techniques, including phishing, financial scam, malicious files, malvertising, financial fraud and browser exploit prevention. Ensuring a safer browsing experience.

SchoolFence is the educational core of the platform, offering training aligned with user behavior, policies, and compliance standards.It includes interactive videos and quizzes, and lets IT managers track progress and issue completion certificates.It turns awareness into continuous, practical experience.


Designed to assess and strengthen user awareness through realistic, context-based simulations. Scenarios are updated monthly using real threat data to highlight vulnerabilities and guide targeted training. Prevent security gaps before real attacks happen.
Unlock the full potential securing your data. Contact us to know more on how use Browserfence & our method.
Process to Succeeded
Getting your team on board has never been easier. Users can register in seconds with just an email address, no complex forms or manual onboarding required. Once registered, all it takes is installing our lightweight browser extension, which works smoothly across all operating systems. That’s it, you’re ready to go, securely and instantly.
With Fency, everything starts with a single click. Launch it, and you instantly unlock interactive training, realistic phishing simulations, and guided protection, all seamlessly integrated into one experience. No need to switch tools or chase down resources. Just click, learn, and stay secure.
At the end of the journey, you get more than just peace of mind. Fency provides detailed reports that clearly show your company’s cybersecurity posture, track improvements over time, and highlight your ongoing commitment to protection. These reports are ready to share with stakeholders, partners, or auditors, making it easy to prove your efforts and stay accountable.

Testimonials
It detects malicious websites, phishing pages, and suspicious requests in real time. It also guides users with clear explanations whenever risky behaviour is detected.
The phishing scenarios are created by Fency’s cybersecurity experts, drawing on over 10 years of red teaming experience from the TeamFence team. This deep expertise allows Fency to design highly customized and realistic training simulations for each organization.
Training is delivered directly through the platform, and users are notified when new modules are available. Everything is tracked and documented automatically.
Yes. Fency understands not just where users go, but how they interact, helping to spot confusion or risky actions and offering immediate, helpful guidance.
Not at all. Fency takes care of everything, including email infrastructure, domain registration, and tracking. You just set the objectives.
Yes. You’ll have access to detailed reports showing completion rates, risky behaviours and improvements over time.